OKX Web3 Security Team: Protecting Your Private Key Like Protecting Your Eyes
Source: OKX

Not Your Keys, Not Your Coins — Decentralized freedom at the cost of absolute "private key security."
A Chainalysis report from July 2025 shows that 17%-23% of Bitcoin is permanently dormant due to private key loss or device damage. Since the private key represents asset ownership, once lost, it cannot be reset, and there is no customer service to help retrieve it. If the key is compromised and the funds are stolen, recovery is nearly impossible. The online world has granted us freedom but has also placed full responsibility back in our hands. As the online ecosystem thrives, various asset theft incidents have occurred frequently. However, individuals often realize it too late and struggle to identify where the issue occurred — Was the private key leaked? Did they click a phishing link? Download malware? Or was it another operational mistake?
The OKX Web3 Security Team aims to enhance everyone's awareness of private key security through this educational content and once again highlight those security blind spots that are often overlooked.
1. Why Might a Private Key or Mnemonic Phrase Leak?
First and foremost, let's correct a common misconception. Many users believe that a private key or mnemonic phrase leak (referred to as "private key leak" hereafter) usually occurs during wallet usage. In reality, if you download and use a wallet through official channels and utilize a wallet from a reputable brand, the private key generally does not leak during normal usage. Private key leaks mostly occur due to improper storage and acquisition by malicious actors. Once someone possesses your private key, they can import it into any wallet and control the account's assets.
In fact, there are many reasons for private key leaks, and the exact source is often challenging to pinpoint completely. However, through analyzing numerous industry cases and assisting in investigations, we have compiled some typical scenarios and clues (as outlined below).

Image: Analysis Challenges in Private Key Theft Shared by SlowMist's Xuandong
2. Common Private Key Leak Scenarios and Mitigation Methods
(1) Most Easily Overlooked Scenario: Leakage During Wallet Creation
Case Study 1: Wallet Creation Assistance by Others. Mr. Li had just started exploring Web3 and, with the help of a "enthusiastic mentor," created a wallet. The mentor assisted him with wallet creation, setting the transaction password, and guided him through deposits and transactions. Although a transaction password was set for the wallet, during the creation process, the mentor had already obtained his private key. A few days later, the 5 ETH Mr. Li had deposited was swiftly transferred out. It was only then he realized that the transaction password was merely for local validation, and anyone with the private key could import it into any wallet and directly transfer his assets.
Security Recommendation: Wallets should be created independently without letting anyone "help" or "act on behalf." If there is suspicion that the private key may have been compromised, assets should promptly be transferred to a new wallet.
Case Study 2: Wallet Creation via Video Conference Screen Sharing. Ms. Zhang, under remote guidance from a "teacher," created a wallet via video conference screen sharing. The teacher demonstrated step by step: downloading the wallet, generating the mnemonic phrase, recharging Gas, and purchasing tokens. The whole process appeared very "intimate," and at the end, she was even reminded, "Never leak your private key to anyone." However, unbeknownst to her, at the moment of screen sharing, the mnemonic phrase might have been recorded. Two weeks later, approximately $12,000 worth of USDT in her account was transferred out.
Security Recommendation: When creating a wallet, disable screen sharing, screen recording, or screen sharing functions. If there is suspicion that the private key may have been compromised, assets should promptly be transferred to a new wallet. Additionally, on the OKX Wallet page displaying the private key and mnemonic phrase, screenshotting, recording, or screen sharing is not allowed, effectively enhancing security.

Image: When screen sharing is detected, OKX Wallet automatically hides the mnemonic phrase and private key, preventing others from viewing the text
(II) Most Common Scenario: Improper Private Key Storage Leading to Leakage
Case Study 3: Fake APP, Nightmare of an Android User. Mr. Wang, a cautious user, took a screenshot of the mnemonic phrase after creating a wallet and stored it in his local photo gallery, never uploading it to the cloud, thinking this was safer. However, he downloaded a so-called "enhanced version of Telegram" from a forum, an APP whose icon and interface were nearly identical to the official version. In reality, it continuously scanned the phone's gallery in the background, used Optical Character Recognition (OCR) technology to identify the mnemonic phrase, and automatically uploaded it to a hacker's server. Three months later, all the assets in Mr. Wang's account were emptied, resulting in a loss exceeding $50,000. Technical analysis revealed that his phone also had fake imToken, MetaMask, Google Authenticator, and other malicious APPs.

Case Four: BOM Malicious App Leading to Mnemonic Leakage. On February 14, 2025, multiple users experienced concentrated wallet asset theft incidents. Through on-chain data analysis, all these theft cases exhibited typical characteristics of mnemonic/private key leakage. Further revisiting the affected users revealed that most of them had previously installed and used an application called BOM. In-depth investigation showed that this application was actually a carefully disguised fraudulent software. Malicious actors, through user authorization manipulation, illegally obtained mnemonic/private key permissions, enabling systematic asset transfer and attempting to conceal their actions.

Security Advice: Many users, out of "convenience," develop habits that are ironically the most dangerous. Therefore, it is recommended that everyone: 1) Do not take a screenshot of the mnemonic phrase! It is suggested to manually copy it on paper and store it in a secure place. 2) When downloading an app, make sure to only use the official channels, and do not easily try unknown "enhanced" versions or third-party modifications. 3) If any device anomalies are detected or if the private key has been screenshot before, do not rely on luck and immediately transfer the assets to a new wallet. 4) What has OKX done? To prevent users from taking screenshots on the private key and mnemonic backup pages, we have disabled the screenshot function on these sensitive pages.

Image: OKX Wallet prohibits screenshots on the private key and mnemonic pages
At the same time, to reduce the risk of users installing fake apps, the Android end also provides a malicious app scanning function.

Image: OKX Wallet on Android provides a malicious app scanning function
(III) The Most Common and Easily Deceived Scenario: Phishing of Private Keys
Case Five: Fake Airdrop Phishing. A well-known NFT project announced on Twitter that they would airdrop a new token to holders. Within just 10 minutes after the announcement, multiple phishing websites appeared at the top of Google search results (promoted via paid advertisements). These phishing websites had domain names with just one letter difference (e.g., opensae.io instead of opensea.io), with page designs almost identical to the official website. When users connected their wallets, the page displayed a prompt: "Network congestion, connection failed, please manually enter your mnemonic phrase to claim the airdrop." On that day, more than 50 users fell for the scam, resulting in a total loss of over $200,000. The quickest victim had their assets transferred out within 3.7 seconds of entering their mnemonic phrase.
Case Six: Social Engineering Attack. Ms. Zhao encountered an operational issue in a project's Discord group. An administrator with an avatar and nickname that looked very "official" proactively private messaged her, claiming to be customer support wanting to help her resolve the issue. They sent her a link to a "verification page." Trusting the administrator, Ms. Zhao clicked on the link and entered her mnemonic phrase as instructed. The page looked exactly like the official website. A few minutes later, multiple assets were continuously transferred out of her wallet. It was only then that she realized the so-called administrator was actually a scammer, and any "customer support" asking users to enter their mnemonic phrase or private key on a website is undoubtedly a scam. It is worth noting that in addition to impersonating official administrators, scammers may also impersonate friends, project team members, or other trusted identities.

Security Advice: A legitimate DApp will never ask you for your private key, and a trustworthy individual will never request your private key from you. Remember: your private key is the key to your assets, so be sure to store it securely and never disclose it easily.
III. Why Can Wallet Providers Do Little Once a Private Key is Compromised?
Some users, upon discovering a suspected private key leak and assets being moved out, will immediately contact the wallet team, hoping that we can provide more assistance. However, in reality, once the private key has been exposed, the space in which wallet providers can intervene is very limited.
Here, let's briefly explain the basic process we follow when receiving reports of "asset theft," and also explain why many times we cannot directly "recover" on-chain assets:
Firstly, we will assist the user in tracing the flow of funds, analyzing whether on-chain funds may be related to known hacker groups or address clusters. At the same time, we will advise the user to quickly transfer any assets that have not been stolen to reduce the risk of further losses. In cases of significant theft, we will recommend that users promptly contact local law enforcement for assistance through legal channels. Our internal team will also conduct a thorough analysis of the incident, summarize the hacker's modus operandi, and provide insights for future user protection.
As a tool provider, wallets themselves cannot freeze or roll back on-chain assets. Once a hacker obtains the private key, they typically use automated scripts to complete the fund transfer within seconds, with a very rapid speed that is difficult to intervene in. Only when the stolen funds eventually flow into a centralized exchange platform is it possible to apply for temporary freezing through legal channels.
When the funds' trajectory is linked to known hacker clusters we are aware of, we will start from their common modus operandi to help users recall if they recently engaged in any high-risk operations, thereby determining at what point the private key may have been exposed.
OKX has always prioritized user fund security, investing heavily over the years to build a risk control system and design multi-factor authentication mechanisms. Although these processes may seem cumbersome, they are all aimed at better protecting user asset security. It can be said that we are also one of the teams in the industry that has invested the most in security.

Image: OKX Wallet Security Score Ranks First
As mentioned earlier, if users lack security awareness or use practices improperly, they may still suffer losses due to reasons such as phishing or private key leakage, regardless of which wallet they use. Therefore, properly safeguarding the private key always remains the most critical security foundation. In addition to continuously enhancing the product's own security capabilities, we also continually strengthen case analysis and share security tips to help users better identify potential risk scenarios.
4. In Summary, Private Key Security Tips
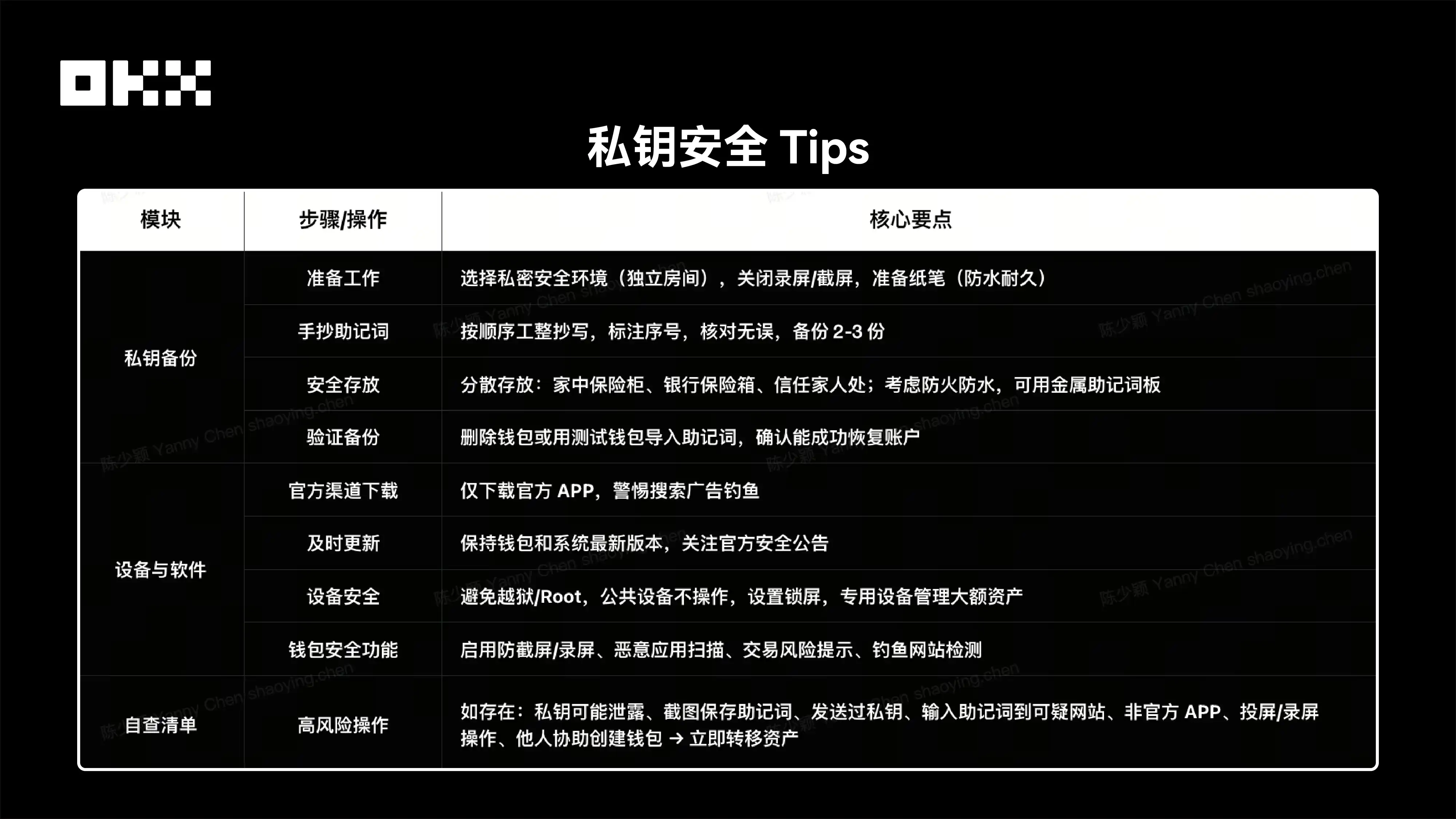
Disclaimer:
This article is for reference only. This article does not intend to provide (i) investment advice or investment recommendations, (ii) an offer, solicitation, or inducement to purchase, sell, or hold digital assets, or (iii) financial, accounting, legal, or tax advice. Digital assets (including stablecoins and NFTs) are subject to market fluctuations, involve high risk, and may depreciate. For questions regarding whether trading or holding digital assets are suitable for you, please consult your legal/tax/investment professional. The OKX Web3 Wallet is only a type of self-custody wallet software service that allows you to discover and interact with third-party platforms, and the OKX Web3 Wallet cannot control the services of such third-party platforms and shall not be held responsible for them. Not all products are available in all regions. You are responsible for understanding and complying with relevant local laws and regulations. The OKX Web3 Wallet and its related services are not provided by the OKX exchange and are governed by the OKX Web3 Ecosystem Service Terms.
This article is contributed content and does not represent the views of BlockBeats.
You may also like

Token Cannot Compound, Where Is the Real Investment Opportunity?

February 6th Market Key Intelligence, How Much Did You Miss?

China's Central Bank and Eight Other Departments' Latest Regulatory Focus: Key Attention to RWA Tokenized Asset Risk
Foreword: Today, the People's Bank of China's website published the "Notice of the People's Bank of China, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration for Market Regulation, China Banking and Insurance Regulatory Commission, China Securities Regulatory Commission, State Administration of Foreign Exchange on Further Preventing and Dealing with Risks Related to Virtual Currency and Others (Yinfa [2026] No. 42)", the latest regulatory requirements from the eight departments including the central bank, which are basically consistent with the regulatory requirements of recent years. The main focus of the regulation is on speculative activities such as virtual currency trading, exchanges, ICOs, overseas platform services, and this time, regulatory oversight of RWA has been added, explicitly prohibiting RWA tokenization, stablecoins (especially those pegged to the RMB). The following is the full text:
To the people's governments of all provinces, autonomous regions, and municipalities directly under the Central Government, the Xinjiang Production and Construction Corps:
Recently, there have been speculative activities related to virtual currency and Real-World Assets (RWA) tokenization, disrupting the economic and financial order and jeopardizing the property security of the people. In order to further prevent and address the risks related to virtual currency and Real-World Assets tokenization, effectively safeguard national security and social stability, in accordance with the "Law of the People's Republic of China on the People's Bank of China," "Law of the People's Republic of China on Commercial Banks," "Securities Law of the People's Republic of China," "Law of the People's Republic of China on Securities Investment Funds," "Law of the People's Republic of China on Futures and Derivatives," "Cybersecurity Law of the People's Republic of China," "Regulations of the People's Republic of China on the Administration of Renminbi," "Regulations on Prevention and Disposal of Illegal Fundraising," "Regulations of the People's Republic of China on Foreign Exchange Administration," "Telecommunications Regulations of the People's Republic of China," and other provisions, after reaching consensus with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, and with the approval of the State Council, the relevant matters are notified as follows:
(I) Virtual currency does not possess the legal status equivalent to fiat currency. Virtual currencies such as Bitcoin, Ether, Tether, etc., have the main characteristics of being issued by non-monetary authorities, using encryption technology and distributed ledger or similar technology, existing in digital form, etc. They do not have legal tender status, should not and cannot be circulated and used as currency in the market.
The business activities related to virtual currency are classified as illegal financial activities. The exchange of fiat currency and virtual currency within the territory, exchange of virtual currencies, acting as a central counterparty in buying and selling virtual currencies, providing information intermediary and pricing services for virtual currency transactions, token issuance financing, and trading of virtual currency-related financial products, etc., fall under illegal financial activities, such as suspected illegal issuance of token vouchers, unauthorized public issuance of securities, illegal operation of securities and futures business, illegal fundraising, etc., are strictly prohibited across the board and resolutely banned in accordance with the law. Overseas entities and individuals are not allowed to provide virtual currency-related services to domestic entities in any form.
A stablecoin pegged to a fiat currency indirectly fulfills some functions of the fiat currency in circulation. Without the consent of relevant authorities in accordance with the law and regulations, any domestic or foreign entity or individual is not allowed to issue a RMB-pegged stablecoin overseas.
(II)Tokenization of Real-World Assets refers to the use of encryption technology and distributed ledger or similar technologies to transform ownership rights, income rights, etc., of assets into tokens (tokens) or other interests or bond certificates with token (token) characteristics, and carry out issuance and trading activities.
Engaging in the tokenization of real-world assets domestically, as well as providing related intermediary, information technology services, etc., which are suspected of illegal issuance of token vouchers, unauthorized public offering of securities, illegal operation of securities and futures business, illegal fundraising, and other illegal financial activities, shall be prohibited; except for relevant business activities carried out with the approval of the competent authorities in accordance with the law and regulations and relying on specific financial infrastructures. Overseas entities and individuals are not allowed to illegally provide services related to the tokenization of real-world assets to domestic entities in any form.
(III) Inter-agency Coordination. The People's Bank of China, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of virtual currency-related illegal financial activities.
The China Securities Regulatory Commission, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of illegal financial activities related to the tokenization of real-world assets.
(IV) Strengthening Local Implementation. The people's governments at the provincial level are overall responsible for the prevention and disposal of risks related to virtual currencies and the tokenization of real-world assets in their respective administrative regions. The specific leading department is the local financial regulatory department, with participation from branches and dispatched institutions of the State Council's financial regulatory department, telecommunications regulators, public security, market supervision, and other departments, in coordination with cyberspace departments, courts, and procuratorates, to improve the normalization of the work mechanism, effectively connect with the relevant work mechanisms of central departments, form a cooperative and coordinated working pattern between central and local governments, effectively prevent and properly handle risks related to virtual currencies and the tokenization of real-world assets, and maintain economic and financial order and social stability.
(5) Enhanced Risk Monitoring. The People's Bank of China, China Securities Regulatory Commission, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration of Foreign Exchange, Cyberspace Administration of China, and other departments continue to improve monitoring techniques and system support, enhance cross-departmental data analysis and sharing, establish sound information sharing and cross-validation mechanisms, promptly grasp the risk situation of activities related to virtual currency and real-world asset tokenization. Local governments at all levels give full play to the role of local monitoring and early warning mechanisms. Local financial regulatory authorities, together with branches and agencies of the State Council's financial regulatory authorities, as well as departments of cyberspace and public security, ensure effective connection between online monitoring, offline investigation, and fund tracking, efficiently and accurately identify activities related to virtual currency and real-world asset tokenization, promptly share risk information, improve early warning information dissemination, verification, and rapid response mechanisms.
(6) Strengthened Oversight of Financial Institutions, Intermediaries, and Technology Service Providers. Financial institutions (including non-bank payment institutions) are prohibited from providing account opening, fund transfer, and clearing services for virtual currency-related business activities, issuing and selling financial products related to virtual currency, including virtual currency and related financial products in the scope of collateral, conducting insurance business related to virtual currency, or including virtual currency in the scope of insurance liability. Financial institutions (including non-bank payment institutions) are prohibited from providing custody, clearing, and settlement services for unauthorized real-world asset tokenization-related business and related financial products. Relevant intermediary institutions and information technology service providers are prohibited from providing intermediary, technical, or other services for unauthorized real-world asset tokenization-related businesses and related financial products.
(7) Enhanced Management of Internet Information Content and Access. Internet enterprises are prohibited from providing online business venues, commercial displays, marketing, advertising, or paid traffic diversion services for virtual currency and real-world asset tokenization-related business activities. Upon discovering clues of illegal activities, they should promptly report to relevant departments and provide technical support and assistance for related investigations and inquiries. Based on the clues transferred by the financial regulatory authorities, the cyberspace administration, telecommunications authorities, and public security departments should promptly close and deal with websites, mobile applications (including mini-programs), and public accounts engaged in virtual currency and real-world asset tokenization-related business activities in accordance with the law.
(8) Strengthened Entity Registration and Advertisement Management. Market supervision departments strengthen entity registration and management, and enterprise and individual business registrations must not contain terms such as "virtual currency," "virtual asset," "cryptocurrency," "crypto asset," "stablecoin," "real-world asset tokenization," or "RWA" in their names or business scopes. Market supervision departments, together with financial regulatory authorities, legally enhance the supervision of advertisements related to virtual currency and real-world asset tokenization, promptly investigating and handling relevant illegal advertisements.
(IX) Continued Rectification of Virtual Currency Mining Activities. The National Development and Reform Commission, together with relevant departments, strictly controls virtual currency mining activities, continuously promotes the rectification of virtual currency mining activities. The people's governments of various provinces take overall responsibility for the rectification of "mining" within their respective administrative regions. In accordance with the requirements of the National Development and Reform Commission and other departments in the "Notice on the Rectification of Virtual Currency Mining Activities" (NDRC Energy-saving Building [2021] No. 1283) and the provisions of the "Guidance Catalog for Industrial Structure Adjustment (2024 Edition)," a comprehensive review, investigation, and closure of existing virtual currency mining projects are conducted, new mining projects are strictly prohibited, and mining machine production enterprises are strictly prohibited from providing mining machine sales and other services within the country.
(X) Severe Crackdown on Related Illegal Financial Activities. Upon discovering clues to illegal financial activities related to virtual currency and the tokenization of real-world assets, local financial regulatory authorities, branches of the State Council's financial regulatory authorities, and other relevant departments promptly investigate, determine, and properly handle the issues in accordance with the law, and seriously hold the relevant entities and individuals legally responsible. Those suspected of crimes are transferred to the judicial authorities for processing according to the law.
(XI) Severe Crackdown on Related Illegal and Criminal Activities. The Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, as well as judicial and procuratorial organs, in accordance with their respective responsibilities, rigorously crack down on illegal and criminal activities related to virtual currency, the tokenization of real-world assets, such as fraud, money laundering, illegal business operations, pyramid schemes, illegal fundraising, and other illegal and criminal activities carried out under the guise of virtual currency, the tokenization of real-world assets, etc.
(XII) Strengthen Industry Self-discipline. Relevant industry associations should enhance membership management and policy advocacy, based on their own responsibilities, advocate and urge member units to resist illegal financial activities related to virtual currency and the tokenization of real-world assets. Member units that violate regulatory policies and industry self-discipline rules are to be disciplined in accordance with relevant self-regulatory management regulations. By leveraging various industry infrastructure, conduct risk monitoring related to virtual currency, the tokenization of real-world assets, and promptly transfer issue clues to relevant departments.
(XIII) Without the approval of relevant departments in accordance with the law and regulations, domestic entities and foreign entities controlled by them may not issue virtual currency overseas.
(XIV) Domestic entities engaging directly or indirectly in overseas external debt-based tokenization of real-world assets, or conducting asset securitization activities abroad based on domestic ownership rights, income rights, etc. (hereinafter referred to as domestic equity), should be strictly regulated in accordance with the principles of "same business, same risk, same rules." The National Development and Reform Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other relevant departments regulate it according to their respective responsibilities. For other forms of overseas real-world asset tokenization activities based on domestic equity by domestic entities, the China Securities Regulatory Commission, together with relevant departments, supervise according to their division of responsibilities. Without the consent and filing of relevant departments, no unit or individual may engage in the above-mentioned business.
(15) Overseas subsidiaries and branches of domestic financial institutions providing Real World Asset Tokenization-related services overseas shall do so legally and prudently. They shall have professional personnel and systems in place to effectively mitigate business risks, strictly implement customer onboarding, suitability management, anti-money laundering requirements, and incorporate them into the domestic financial institutions' compliance and risk management system. Intermediaries and information technology service providers offering Real World Asset Tokenization services abroad based on domestic equity or conducting Real World Asset Tokenization business in the form of overseas debt for domestic entities directly or indirectly venturing abroad must strictly comply with relevant laws and regulations. They should establish and improve relevant compliance and internal control systems in accordance with relevant normative requirements, strengthen business and risk control, and report the business developments to the relevant regulatory authorities for approval or filing.
(16) Strengthen organizational leadership and overall coordination. All departments and regions should attach great importance to the prevention of risks related to virtual currencies and Real World Asset Tokenization, strengthen organizational leadership, clarify work responsibilities, form a long-term effective working mechanism with centralized coordination, local implementation, and shared responsibilities, maintain high pressure, dynamically monitor risks, effectively prevent and mitigate risks in an orderly and efficient manner, legally protect the property security of the people, and make every effort to maintain economic and financial order and social stability.
(17) Widely carry out publicity and education. All departments, regions, and industry associations should make full use of various media and other communication channels to disseminate information through legal and policy interpretation, analysis of typical cases, and education on investment risks, etc. They should promote the illegality and harm of virtual currencies and Real World Asset Tokenization-related businesses and their manifestations, fully alert to potential risks and hidden dangers, and enhance public awareness and identification capabilities for risk prevention.
(18) Engaging in illegal financial activities related to virtual currencies and Real World Asset Tokenization in violation of this notice, as well as providing services for virtual currencies and Real World Asset Tokenization-related businesses, shall be punished in accordance with relevant regulations. If it constitutes a crime, criminal liability shall be pursued according to the law. For domestic entities and individuals who knowingly or should have known that overseas entities illegally provided virtual currency or Real World Asset Tokenization-related services to domestic entities and still assisted them, relevant responsibilities shall be pursued according to the law. If it constitutes a crime, criminal liability shall be pursued according to the law.
(19) If any unit or individual invests in virtual currencies, Real World Asset Tokens, and related financial products against public order and good customs, the relevant civil legal actions shall be invalid, and any resulting losses shall be borne by them. If there are suspicions of disrupting financial order and jeopardizing financial security, the relevant departments shall deal with them according to the law.
This notice shall enter into force upon the date of its issuance. The People's Bank of China and ten other departments' "Notice on Further Preventing and Dealing with the Risks of Virtual Currency Trading Speculation" (Yinfa [2021] No. 237) is hereby repealed.

Former Partner's Perspective on Multicoin: Kyle's Exit, But the Game He Left Behind Just Getting Started

Why Bitcoin Is Falling Now: The Real Reasons Behind BTC's Crash & WEEX's Smart Profit Playbook
Bitcoin's ongoing crash explained: Discover the 5 hidden triggers behind BTC's plunge & how WEEX's Auto Earn and Trade to Earn strategies help traders profit from crypto market volatility.

Wall Street's Hottest Trades See Exodus

Vitalik Discusses Ethereum Scaling Path, Circle Announces Partnership with Polymarket, What's the Overseas Crypto Community Talking About Today?

Believing in the Capital Markets - The Essence and Core Value of Cryptocurrency

Polymarket's 'Weatherman': Predict Temperature, Win Million-Dollar Payout

$15K+ Profits: The 4 AI Trading Secrets WEEX Hackathon Prelim Winners Used to Dominate Volatile Crypto Markets
How WEEX Hackathon's top AI trading strategies made $15K+ in crypto markets: 4 proven rules for ETH/BTC trading, market structure analysis, and risk management in volatile conditions.

A nearly 20% one-day plunge, how long has it been since you last saw a $60,000 Bitcoin?

Raoul Pal: I've seen every single panic, and they are never the end.

Key Market Information Discrepancy on February 6th - A Must-Read! | Alpha Morning Report

2026 Crypto Industry's First Snowfall

The Harsh Reality Behind the $26 Billion Crypto Liquidation: Liquidity Is Killing the Market

Why Is Gold, US Stocks, Bitcoin All Falling?

Key Market Intelligence for February 5th, how much did you miss out on?

Wintermute: By 2026, crypto had gradually become the settlement layer of the Internet economy
Token Cannot Compound, Where Is the Real Investment Opportunity?
February 6th Market Key Intelligence, How Much Did You Miss?
China's Central Bank and Eight Other Departments' Latest Regulatory Focus: Key Attention to RWA Tokenized Asset Risk
Foreword: Today, the People's Bank of China's website published the "Notice of the People's Bank of China, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration for Market Regulation, China Banking and Insurance Regulatory Commission, China Securities Regulatory Commission, State Administration of Foreign Exchange on Further Preventing and Dealing with Risks Related to Virtual Currency and Others (Yinfa [2026] No. 42)", the latest regulatory requirements from the eight departments including the central bank, which are basically consistent with the regulatory requirements of recent years. The main focus of the regulation is on speculative activities such as virtual currency trading, exchanges, ICOs, overseas platform services, and this time, regulatory oversight of RWA has been added, explicitly prohibiting RWA tokenization, stablecoins (especially those pegged to the RMB). The following is the full text:
To the people's governments of all provinces, autonomous regions, and municipalities directly under the Central Government, the Xinjiang Production and Construction Corps:
Recently, there have been speculative activities related to virtual currency and Real-World Assets (RWA) tokenization, disrupting the economic and financial order and jeopardizing the property security of the people. In order to further prevent and address the risks related to virtual currency and Real-World Assets tokenization, effectively safeguard national security and social stability, in accordance with the "Law of the People's Republic of China on the People's Bank of China," "Law of the People's Republic of China on Commercial Banks," "Securities Law of the People's Republic of China," "Law of the People's Republic of China on Securities Investment Funds," "Law of the People's Republic of China on Futures and Derivatives," "Cybersecurity Law of the People's Republic of China," "Regulations of the People's Republic of China on the Administration of Renminbi," "Regulations on Prevention and Disposal of Illegal Fundraising," "Regulations of the People's Republic of China on Foreign Exchange Administration," "Telecommunications Regulations of the People's Republic of China," and other provisions, after reaching consensus with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, and with the approval of the State Council, the relevant matters are notified as follows:
(I) Virtual currency does not possess the legal status equivalent to fiat currency. Virtual currencies such as Bitcoin, Ether, Tether, etc., have the main characteristics of being issued by non-monetary authorities, using encryption technology and distributed ledger or similar technology, existing in digital form, etc. They do not have legal tender status, should not and cannot be circulated and used as currency in the market.
The business activities related to virtual currency are classified as illegal financial activities. The exchange of fiat currency and virtual currency within the territory, exchange of virtual currencies, acting as a central counterparty in buying and selling virtual currencies, providing information intermediary and pricing services for virtual currency transactions, token issuance financing, and trading of virtual currency-related financial products, etc., fall under illegal financial activities, such as suspected illegal issuance of token vouchers, unauthorized public issuance of securities, illegal operation of securities and futures business, illegal fundraising, etc., are strictly prohibited across the board and resolutely banned in accordance with the law. Overseas entities and individuals are not allowed to provide virtual currency-related services to domestic entities in any form.
A stablecoin pegged to a fiat currency indirectly fulfills some functions of the fiat currency in circulation. Without the consent of relevant authorities in accordance with the law and regulations, any domestic or foreign entity or individual is not allowed to issue a RMB-pegged stablecoin overseas.
(II)Tokenization of Real-World Assets refers to the use of encryption technology and distributed ledger or similar technologies to transform ownership rights, income rights, etc., of assets into tokens (tokens) or other interests or bond certificates with token (token) characteristics, and carry out issuance and trading activities.
Engaging in the tokenization of real-world assets domestically, as well as providing related intermediary, information technology services, etc., which are suspected of illegal issuance of token vouchers, unauthorized public offering of securities, illegal operation of securities and futures business, illegal fundraising, and other illegal financial activities, shall be prohibited; except for relevant business activities carried out with the approval of the competent authorities in accordance with the law and regulations and relying on specific financial infrastructures. Overseas entities and individuals are not allowed to illegally provide services related to the tokenization of real-world assets to domestic entities in any form.
(III) Inter-agency Coordination. The People's Bank of China, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of virtual currency-related illegal financial activities.
The China Securities Regulatory Commission, together with the National Development and Reform Commission, the Ministry of Industry and Information Technology, the Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the State Administration of Foreign Exchange, and other departments, will improve the work mechanism, strengthen coordination with the Cyberspace Administration of China, the Supreme People's Court, and the Supreme People's Procuratorate, coordinate efforts, and overall guide regions to carry out risk prevention and disposal of illegal financial activities related to the tokenization of real-world assets.
(IV) Strengthening Local Implementation. The people's governments at the provincial level are overall responsible for the prevention and disposal of risks related to virtual currencies and the tokenization of real-world assets in their respective administrative regions. The specific leading department is the local financial regulatory department, with participation from branches and dispatched institutions of the State Council's financial regulatory department, telecommunications regulators, public security, market supervision, and other departments, in coordination with cyberspace departments, courts, and procuratorates, to improve the normalization of the work mechanism, effectively connect with the relevant work mechanisms of central departments, form a cooperative and coordinated working pattern between central and local governments, effectively prevent and properly handle risks related to virtual currencies and the tokenization of real-world assets, and maintain economic and financial order and social stability.
(5) Enhanced Risk Monitoring. The People's Bank of China, China Securities Regulatory Commission, National Development and Reform Commission, Ministry of Industry and Information Technology, Ministry of Public Security, State Administration of Foreign Exchange, Cyberspace Administration of China, and other departments continue to improve monitoring techniques and system support, enhance cross-departmental data analysis and sharing, establish sound information sharing and cross-validation mechanisms, promptly grasp the risk situation of activities related to virtual currency and real-world asset tokenization. Local governments at all levels give full play to the role of local monitoring and early warning mechanisms. Local financial regulatory authorities, together with branches and agencies of the State Council's financial regulatory authorities, as well as departments of cyberspace and public security, ensure effective connection between online monitoring, offline investigation, and fund tracking, efficiently and accurately identify activities related to virtual currency and real-world asset tokenization, promptly share risk information, improve early warning information dissemination, verification, and rapid response mechanisms.
(6) Strengthened Oversight of Financial Institutions, Intermediaries, and Technology Service Providers. Financial institutions (including non-bank payment institutions) are prohibited from providing account opening, fund transfer, and clearing services for virtual currency-related business activities, issuing and selling financial products related to virtual currency, including virtual currency and related financial products in the scope of collateral, conducting insurance business related to virtual currency, or including virtual currency in the scope of insurance liability. Financial institutions (including non-bank payment institutions) are prohibited from providing custody, clearing, and settlement services for unauthorized real-world asset tokenization-related business and related financial products. Relevant intermediary institutions and information technology service providers are prohibited from providing intermediary, technical, or other services for unauthorized real-world asset tokenization-related businesses and related financial products.
(7) Enhanced Management of Internet Information Content and Access. Internet enterprises are prohibited from providing online business venues, commercial displays, marketing, advertising, or paid traffic diversion services for virtual currency and real-world asset tokenization-related business activities. Upon discovering clues of illegal activities, they should promptly report to relevant departments and provide technical support and assistance for related investigations and inquiries. Based on the clues transferred by the financial regulatory authorities, the cyberspace administration, telecommunications authorities, and public security departments should promptly close and deal with websites, mobile applications (including mini-programs), and public accounts engaged in virtual currency and real-world asset tokenization-related business activities in accordance with the law.
(8) Strengthened Entity Registration and Advertisement Management. Market supervision departments strengthen entity registration and management, and enterprise and individual business registrations must not contain terms such as "virtual currency," "virtual asset," "cryptocurrency," "crypto asset," "stablecoin," "real-world asset tokenization," or "RWA" in their names or business scopes. Market supervision departments, together with financial regulatory authorities, legally enhance the supervision of advertisements related to virtual currency and real-world asset tokenization, promptly investigating and handling relevant illegal advertisements.
(IX) Continued Rectification of Virtual Currency Mining Activities. The National Development and Reform Commission, together with relevant departments, strictly controls virtual currency mining activities, continuously promotes the rectification of virtual currency mining activities. The people's governments of various provinces take overall responsibility for the rectification of "mining" within their respective administrative regions. In accordance with the requirements of the National Development and Reform Commission and other departments in the "Notice on the Rectification of Virtual Currency Mining Activities" (NDRC Energy-saving Building [2021] No. 1283) and the provisions of the "Guidance Catalog for Industrial Structure Adjustment (2024 Edition)," a comprehensive review, investigation, and closure of existing virtual currency mining projects are conducted, new mining projects are strictly prohibited, and mining machine production enterprises are strictly prohibited from providing mining machine sales and other services within the country.
(X) Severe Crackdown on Related Illegal Financial Activities. Upon discovering clues to illegal financial activities related to virtual currency and the tokenization of real-world assets, local financial regulatory authorities, branches of the State Council's financial regulatory authorities, and other relevant departments promptly investigate, determine, and properly handle the issues in accordance with the law, and seriously hold the relevant entities and individuals legally responsible. Those suspected of crimes are transferred to the judicial authorities for processing according to the law.
(XI) Severe Crackdown on Related Illegal and Criminal Activities. The Ministry of Public Security, the People's Bank of China, the State Administration for Market Regulation, the China Banking and Insurance Regulatory Commission, the China Securities Regulatory Commission, as well as judicial and procuratorial organs, in accordance with their respective responsibilities, rigorously crack down on illegal and criminal activities related to virtual currency, the tokenization of real-world assets, such as fraud, money laundering, illegal business operations, pyramid schemes, illegal fundraising, and other illegal and criminal activities carried out under the guise of virtual currency, the tokenization of real-world assets, etc.
(XII) Strengthen Industry Self-discipline. Relevant industry associations should enhance membership management and policy advocacy, based on their own responsibilities, advocate and urge member units to resist illegal financial activities related to virtual currency and the tokenization of real-world assets. Member units that violate regulatory policies and industry self-discipline rules are to be disciplined in accordance with relevant self-regulatory management regulations. By leveraging various industry infrastructure, conduct risk monitoring related to virtual currency, the tokenization of real-world assets, and promptly transfer issue clues to relevant departments.
(XIII) Without the approval of relevant departments in accordance with the law and regulations, domestic entities and foreign entities controlled by them may not issue virtual currency overseas.
(XIV) Domestic entities engaging directly or indirectly in overseas external debt-based tokenization of real-world assets, or conducting asset securitization activities abroad based on domestic ownership rights, income rights, etc. (hereinafter referred to as domestic equity), should be strictly regulated in accordance with the principles of "same business, same risk, same rules." The National Development and Reform Commission, the China Securities Regulatory Commission, the State Administration of Foreign Exchange, and other relevant departments regulate it according to their respective responsibilities. For other forms of overseas real-world asset tokenization activities based on domestic equity by domestic entities, the China Securities Regulatory Commission, together with relevant departments, supervise according to their division of responsibilities. Without the consent and filing of relevant departments, no unit or individual may engage in the above-mentioned business.
(15) Overseas subsidiaries and branches of domestic financial institutions providing Real World Asset Tokenization-related services overseas shall do so legally and prudently. They shall have professional personnel and systems in place to effectively mitigate business risks, strictly implement customer onboarding, suitability management, anti-money laundering requirements, and incorporate them into the domestic financial institutions' compliance and risk management system. Intermediaries and information technology service providers offering Real World Asset Tokenization services abroad based on domestic equity or conducting Real World Asset Tokenization business in the form of overseas debt for domestic entities directly or indirectly venturing abroad must strictly comply with relevant laws and regulations. They should establish and improve relevant compliance and internal control systems in accordance with relevant normative requirements, strengthen business and risk control, and report the business developments to the relevant regulatory authorities for approval or filing.
(16) Strengthen organizational leadership and overall coordination. All departments and regions should attach great importance to the prevention of risks related to virtual currencies and Real World Asset Tokenization, strengthen organizational leadership, clarify work responsibilities, form a long-term effective working mechanism with centralized coordination, local implementation, and shared responsibilities, maintain high pressure, dynamically monitor risks, effectively prevent and mitigate risks in an orderly and efficient manner, legally protect the property security of the people, and make every effort to maintain economic and financial order and social stability.
(17) Widely carry out publicity and education. All departments, regions, and industry associations should make full use of various media and other communication channels to disseminate information through legal and policy interpretation, analysis of typical cases, and education on investment risks, etc. They should promote the illegality and harm of virtual currencies and Real World Asset Tokenization-related businesses and their manifestations, fully alert to potential risks and hidden dangers, and enhance public awareness and identification capabilities for risk prevention.
(18) Engaging in illegal financial activities related to virtual currencies and Real World Asset Tokenization in violation of this notice, as well as providing services for virtual currencies and Real World Asset Tokenization-related businesses, shall be punished in accordance with relevant regulations. If it constitutes a crime, criminal liability shall be pursued according to the law. For domestic entities and individuals who knowingly or should have known that overseas entities illegally provided virtual currency or Real World Asset Tokenization-related services to domestic entities and still assisted them, relevant responsibilities shall be pursued according to the law. If it constitutes a crime, criminal liability shall be pursued according to the law.
(19) If any unit or individual invests in virtual currencies, Real World Asset Tokens, and related financial products against public order and good customs, the relevant civil legal actions shall be invalid, and any resulting losses shall be borne by them. If there are suspicions of disrupting financial order and jeopardizing financial security, the relevant departments shall deal with them according to the law.
This notice shall enter into force upon the date of its issuance. The People's Bank of China and ten other departments' "Notice on Further Preventing and Dealing with the Risks of Virtual Currency Trading Speculation" (Yinfa [2021] No. 237) is hereby repealed.
Former Partner's Perspective on Multicoin: Kyle's Exit, But the Game He Left Behind Just Getting Started
Why Bitcoin Is Falling Now: The Real Reasons Behind BTC's Crash & WEEX's Smart Profit Playbook
Bitcoin's ongoing crash explained: Discover the 5 hidden triggers behind BTC's plunge & how WEEX's Auto Earn and Trade to Earn strategies help traders profit from crypto market volatility.

 Earn
Earn